phthalmic muscles
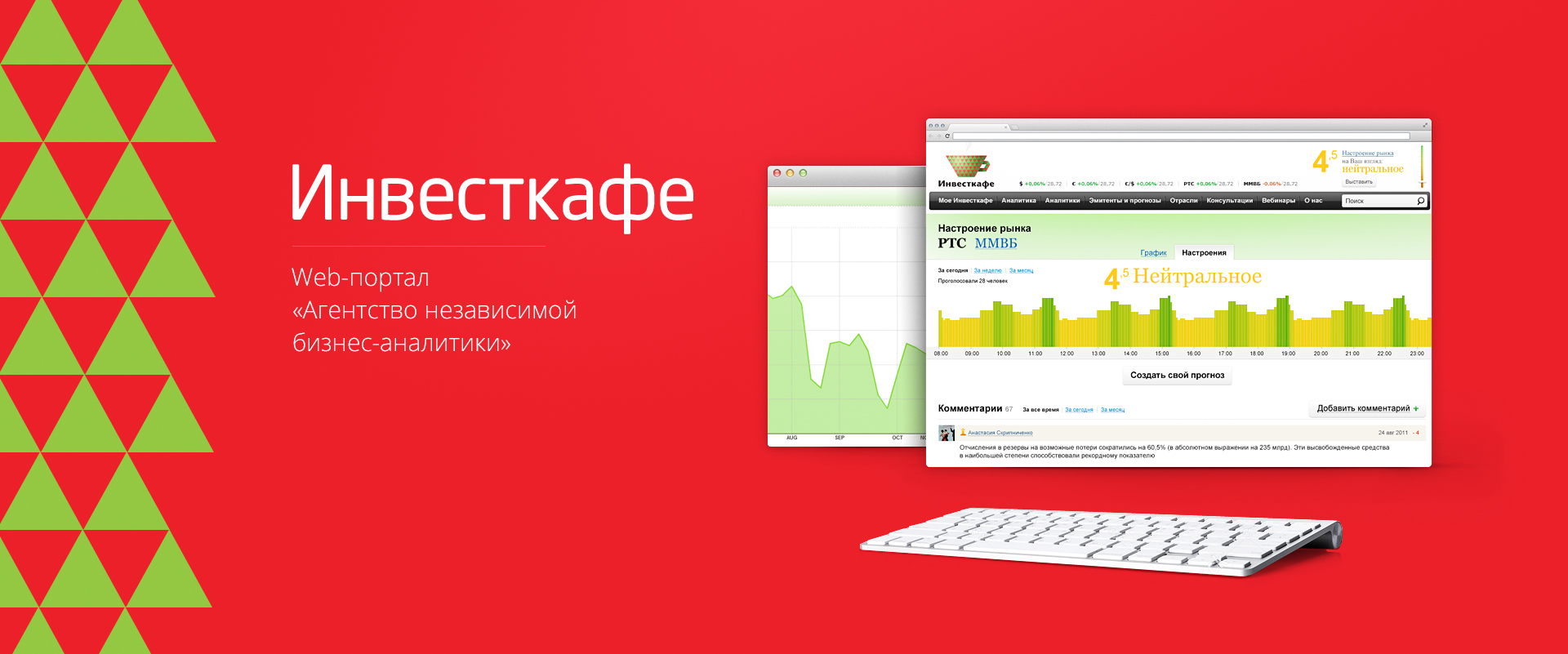
The main elements of the modern site.
 Elements of a modern web site.
Elements of a modern web site.
So from the first estimate, it is certainly difficult to identify the main features of a modern web site. But I still try to do it. Web design is closer to art than to artisan creation, and like any art can not be defined by clear definitions and regulations. However, now there are several criteria that a modern web site must meet. Continue reading
To help the site customer and future users: Customer errors
 It is not a secret to anyone that a human being is far from being perfect and can be mistaken. The consequences of this affect both himself and his surroundings. The biggest problem is that he is often unable to understand what his mistakes are and, therefore, he cannot correct them either. This applies to all human activities without exception. Continue reading
It is not a secret to anyone that a human being is far from being perfect and can be mistaken. The consequences of this affect both himself and his surroundings. The biggest problem is that he is often unable to understand what his mistakes are and, therefore, he cannot correct them either. This applies to all human activities without exception. Continue reading
Vector Ulan-Ude – a reliable satellite in the city
 If you possess the necessary information for you, then you will be able to correctly apply them and emerge as the winner of any situation. Today, a new project has emerged that facilitates the search for the necessary, desired information. This project was created in Ulan-Ude. The name given to this innovation was “Vector of Ulan-Ude”. Continue reading
If you possess the necessary information for you, then you will be able to correctly apply them and emerge as the winner of any situation. Today, a new project has emerged that facilitates the search for the necessary, desired information. This project was created in Ulan-Ude. The name given to this innovation was “Vector of Ulan-Ude”. Continue reading